Malware Quickbytes: Python Stealer
Malware Quickbytes is a series where a sample is analysed briefly, often using shortcuts.
Sample
I came across an untagged sample uploaded to Malware Bazaar: Sample
SHA256: e5287f2e60151676f861ab0825152d444371063880ab98dc6bcb796bf577525b
So, let’s analyse it.
Analysis
From the tria.ge report , the sample seems to be a stealer. The report also mentions the following:
- Dropping a file to the startup location
- Fetches the external ip addresses
- Reads browser files.
- Reads wifi configuration
- Uses discord as a c2.
The report doesn’t mention the name of the stealer so let’s dig deeper.
I took a look at the unpac.me report
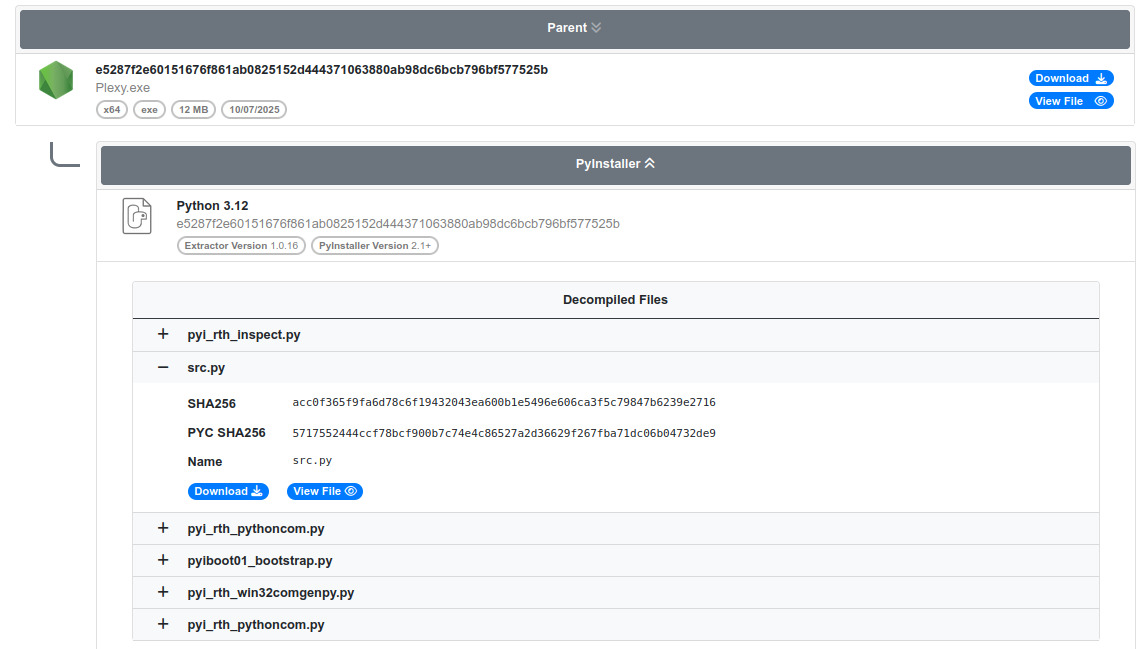
According to the unpac.me report, the sample is packed using PyInstaller and targets Python 3.12. It has extracted all the files and decompiled .pyc files.
The malware source code is the decompiled src.py file.
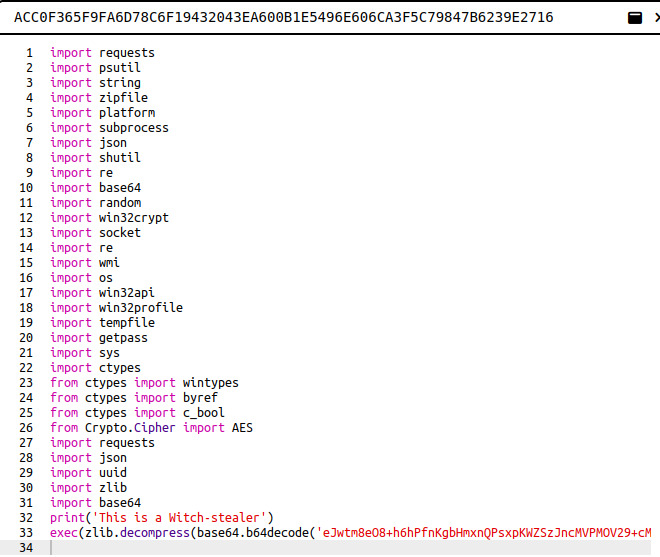
As seen in the figure above, after the imports there is a line which contains a base64-encoded string. The string is base64-decoded and decompressed with zlib before being executed with exec. It also prints the string This is Witch-stealer.
In order to see the actual code that is executed, I rewrote the decompiled Python code by replacing the exec with print and removing unused imports.
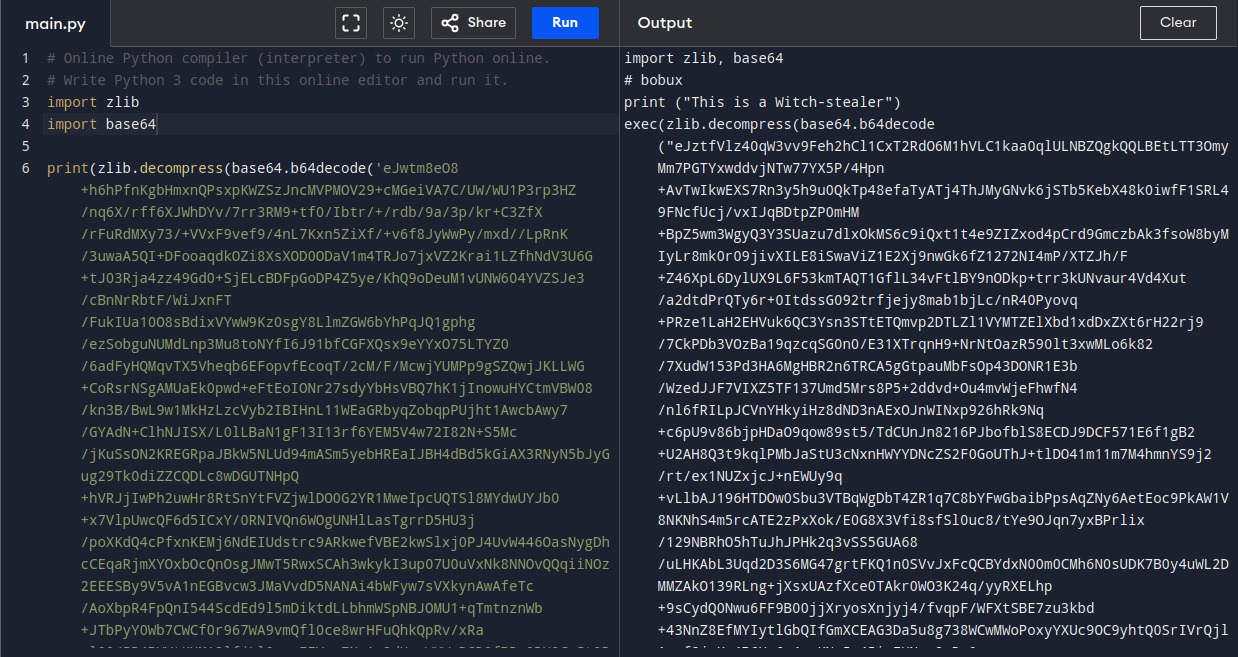
The output of the rewritten code shows a python code which also contains a base64 encoded string that is base64 decoded and decompressed using zlib before being executed using exec. I rewrote it again by replacing exec with print
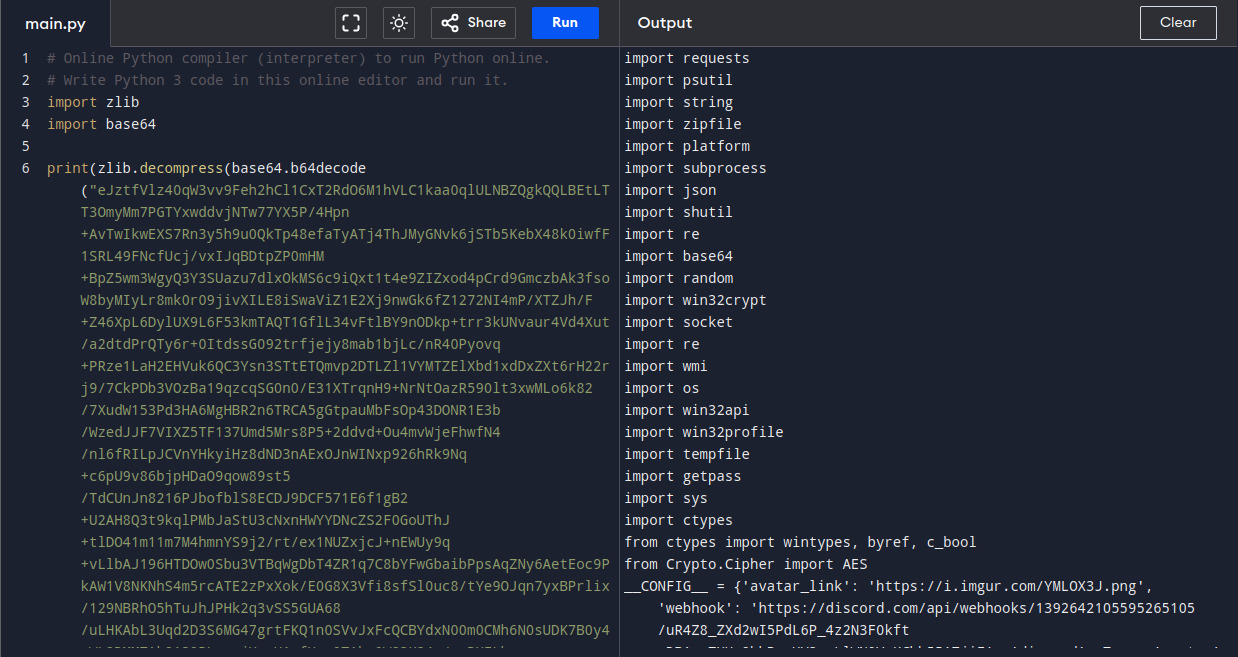
The output finally shows the entire stealer code which is written in python. See this gist for the full code.
The source code contains imports defined in the middle of the code which is atypical for human-written code. This indicates that the author may have copy-pasted the code from another source or used AI tools such as Copilot for coding.
Summary
Summarizing only the main aspects of this malware:
-
Configuration
{
'avatar_link': 'https://i.imgur.com/YMLOX3J.png',
'webhook': 'https://discord.com/api/webhooks/1392642105595265105/uR4Z8_ZXd2wI5PdL6P_4z2N3F0kft-DB1ocTXHn8hbPnsHY3agLlWN0VvKCbh55AZjiE',
'discord': True,
'system': True,
'startup': True,
'minecraft': True,
'Steam': True,
'Anti_Debugs_VM': True,
'backupcode': True,
'ERROR': True,
'Telegram': False
}It contains a webhook, which serves as the C2 for the malware. Other options determine which features of the stealer must be executed.
-
Anti-VM checks
- It contains a list of HWIDs, PC Names, Usernames and external IP address. If a machine matches any of them, the malware attempts to cause a blue screen of death (BSOD) by either raising a Winlong Fatal Error or killing explorer.exe but only when executed on a Windows system.
- It then deletes itself by writing a .bat file to the temporary folder when running on a Windows system. The .bat file, upon execution, deletes the executable from disk.
-
Stealing data
- It steals user login data from applications such as
- Steam
- Kills the process, zips configuration files and session data, and uploads the archive to the webhook.
- Telegram
- Copies the tdata folder and uploads it as a zip file to gofile.io.
- Discord
- Accesses login data stored in Chromium-based browsers (e.g., Brave, Yandex, Iridium) and looks specifically for Discord login tokens.
- Steals Discord backup codes if a file named discord_backup_codes.txt is found in
Downloadsfolder.
- Minecraft
- Searches for Minecraft launcher files (e.g., launcher_accounts.json, usercache.json) in the AppData folder and sends truncated contents to the webhook.
- Steam
- It steals user login data from applications such as
-
Copying itself to Startup and Displaying Fake Error
- It copies itself to
Startupfor persistence. - It also shows a fake error message to trick end users.
- It copies itself to
-
System Information Gathering
- It gathers information about the system such as:
- Hostname/Computername
- Username
- GPU
- HWID
- Wifi information such as name and password.
- CPU Processor
- Operating System
- It gathers information about the system such as:
-
Exfiltration
- The data is sent to C2 server as JSON objects over a POST request. The JSON objects contain the field:
username: Candy Stealeramong other fields.
- The data is sent to C2 server as JSON objects over a POST request. The JSON objects contain the field:
Identification
The malware when executed prints a string This is Witch-stealer; however, when sending the data, it uses the string Candy Stealer. A network-based indicator is generally stronger than a printed string for malware identification. Also, the string This is Witch-stealer is only present in the initial stages of extracting the stealer source code but not in the final source code. Therefore, I would classify this malware as “Candy Stealer”.